VPN
Introduction
This document describes a small (up to 253 node) server configuration wireguard network. Throughout a wireguard network IP is referred to as a.a.a.0/24, a typical node as a.a.a.x (x is replaced with another letter if it’s necessary to distinguish between nodes).
The servers public key is referred to as
sssssssssssssssssssssssssssssssssssssssss= and the servers public ip
as s.s.s.s and port sssss.
A client’s public key is referred to using another single letter string
(e.g yyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyy=) and it’s public ip and
port using the same letter (e.g y.y.y.y and yyyyy).
Server
Using wireguard in a server configuration, clients simply have the server in the
Peer section. The server has all clients in the Peer section. All
communications are inniated through the server.
Below is an example salt configuration (e.g. /srv/pillar/sites/my-vpn.sls)
for a vpn server with 2 peers that also acts as a DNS server for the wireguard
network (this is a very simplified example you may also want to add
forwarders and allowed_ips etc.)
A node’s public key and IP Address needs to be added to the vpn section
but the ip address only needs to be added to the dns section if it needs
to be looked up, in this example only the server and the DNS/VPN server
can be looked up.
Add the IP address to the dns, zones and vpn sections e.g for a
network with 3 nodes:
- vpn server with an ip of a.a.a.1 (e.g. 10.10.10.1),
- a server with ip of a.a.a.11
- and a client with a.a.a.101
server_meta:
dns:
zones:
- name: db.my.lan
serial 1
zone: my.lan
primary_server: ns.my.lan
email_address: root.my.lan
entries:
- { name: '', type: A, value: a.a.a.1 }
- { name: '@', type: NS, value: ns.my.lan }
- { name: '@', type: A, value: a.a.a.1 }
- { name: server, type: A, value: a.a.a.11 }
vpn:
interface: wgx
conf:
Address: a.a.a.1
PrivateKey: SSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSSS=
ListenPort: sssss
DNS: a.a.a.1
peers:
server:
PublicKey: yyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyyy=
AllowedIPs: a.a.a.11/32
client:
PublicKey: zzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzzz=
AllowedIPs: a.a.a.101/32
Once the configuration for the node is added the salt state needs to be applied to the vpn server…
Server VPN (New)
To create a new VPN server:
Create a new server (in the cloud).
Connect the new server to our company VPN (and Salt) using the
salt-minion-setupscript.
Questions
What is
forwardersand why is it the same on different VPNs?What is
serialinsidezones?Why are there multiple zones?
Does
peersneed aserver? Why? What should it be?When creating the VPN
sshd_interface_ips(the sshListenAddress) is listening on the Wireguard interface, but no clients are yet created. Or… can we just use the script to create a client?
Client (Linux)
Tip
Before installing Ubuntu Linux, decide on the hostname
(e.g. cloud-a)
This will make the Salt configuration much easier to do.
Tip
When installing Linux, do not use an existing username. Salt creates users with fixed UUID.
We’ve written a private script that installs salt configuration management and
wireguard packages and creates a wireguard configuration for our vpn.
Internally we use this salt-minion-setup script to allow linux nodes to
request to be part of our configuration management and internal vpn. These then
need to be accepted on the salt master and added to the piller configuration
file (see above) for the vpn servers and the state applied to it:
The
salt-minion-setupscript creates the private and public keys on the client and displays the peer information to be added to the server on the screen this can then be cut and pasted into thesites/my-vpn.slsin the pillar file on the Salt master.Apply the states.
Restart the interface (
wg-quick down wg0 && wg-quick up wg0).
Tip
Don’t forget to setup the Wireguard - Configuration
Client (Windows)
Download and install Wireguard https://www.wireguard.com/install/
Log in as an administrator and Create a new connection (Add empty tunnel) This will create an ini file with a public and private key. Alternatively the configuration file could be created on a separate server and imported.
Using either method your configuration should contain the following directives:
[Interface]
PrivateKey = CCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCCC=
Address = a.a.a.<Free node number>/32
DNS = a.a.a.1
[Peer]
PublicKey = sssssssssssssssssssssssssssssssssssssssssssssss=
AllowedIPs = a.a.a.0/24
Endpoint = vpn-my.hatherleigh.info:sssss
PersistentKeepalive = 25
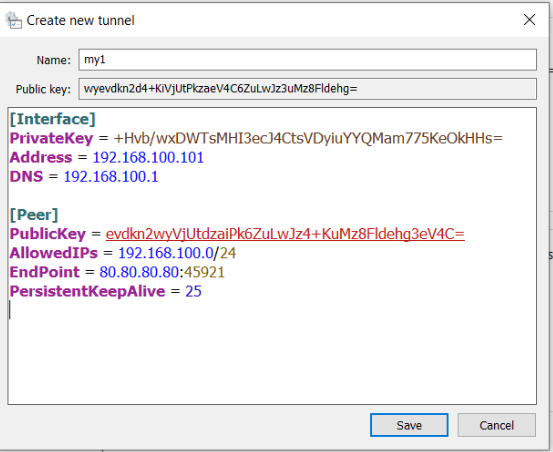
Save and Activate
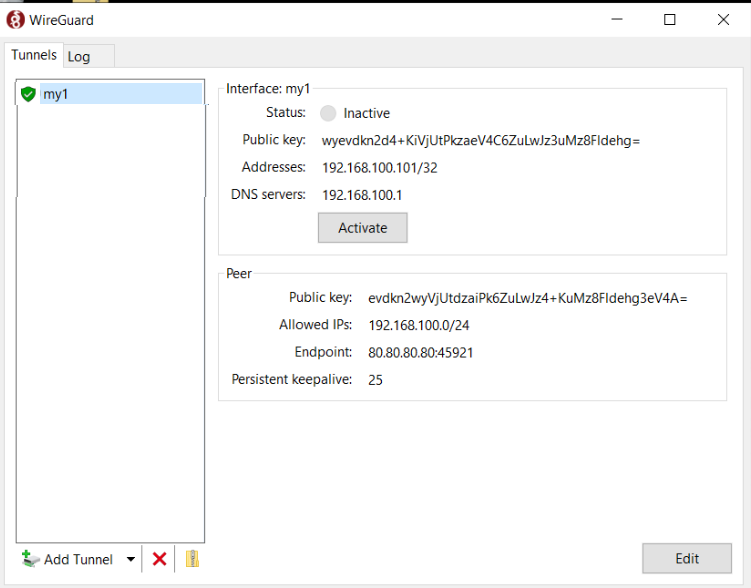
The Public key and IP address need to be added to your Salt pillar for your VPN server and the states applied.
Tailscale
From Using Tailscale with your firewall,
Most of the time, Tailscale should work with your firewall out of the box. Thanks to NAT traversal, nodes in your tailnet can connect directly peer to peer, even through firewalls.
For the Digital Ocean Firewall, we can remove all Inbound Rules.