Microsoft Azure
Links
email
To create an email address for a user, create the user in the Azure portal (https://portal.azure.com/) then browse to email in the Office 365 admin.
OpenID Connect
Is used by the login app. See OpenID Connect for more information.
Create Directory
Create your directory at https://portal.azure.com/

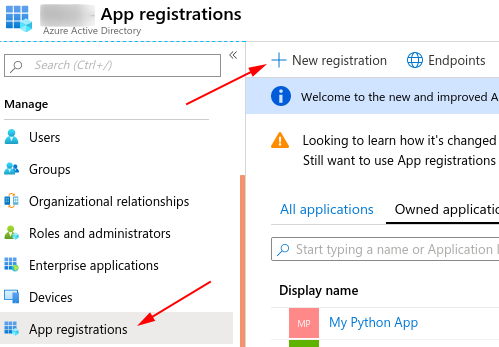
Register application
Register your application:
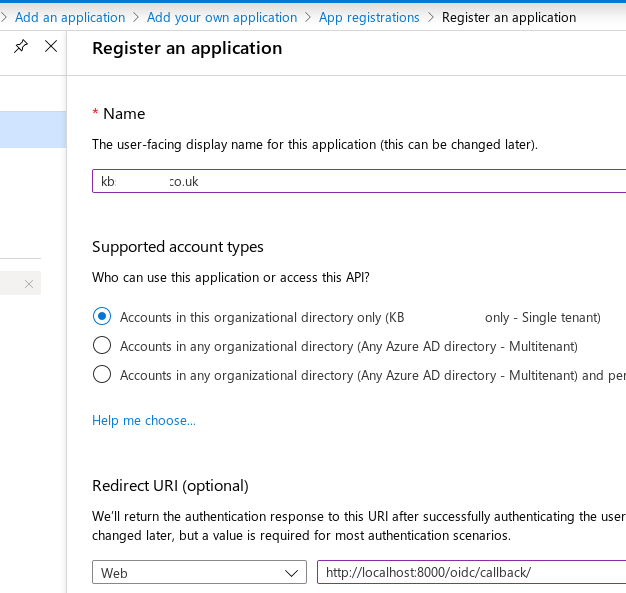
Add a Redirect URI for the Django (and Ember apps)…
Start by finding the Django URL:
# www.hatherleigh.info.sh shell
import urllib.parse
from django.conf import settings
from django.urls import reverse
urllib.parse.urljoin(settings.HOST_NAME, reverse('oidc_authentication_callback'))
Then add the Django URL e.g:
https://www.hatherleigh.info/back/oidc/callback/
Tip
Don’t forget to append a /.
Tip
If you forget to add a Redirect URI or set it incorrectly, the error message from Azure Sign in will be, The reply URL specified in the request does not match the reply URLs configured for the application.
Ember
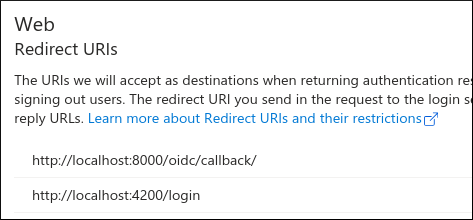
Add a Redirect URI e.g:
https://www.hatherleigh.info/login
Or for development:
http://localhost:4200/login
Warning
Do NOT append a backslash for the Ember URLs.
Update front/config/environment.js with the
if (environment === "development") {
ENV["oidcAuth"]["clientId"] = "0cc7e...",
ENV["oidcAuth"]["host"] = "https://login.microsoftonline.com/bcb19.../oauth2/v2.0"
}
So for a Django and Ember app on a development machine, the Redirect URIs will look like this:
Update
You can update the redirect URIs by selecting Redirect URIs in the application overview:
Warning
You will need to append a / to the Redirect URI
(e.g. http://localhost:8000/oidc/callback/).
Tip
For more information, see examples of callback urls in mozilla-django-oidc,
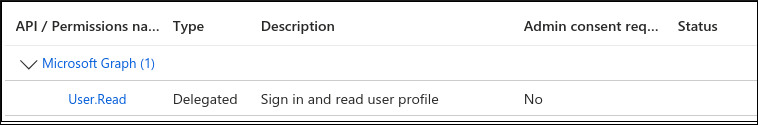
API permissions
Check the API permissions and set the Status to Granted… for
User.Read:
Settings
The login app requires a .private file containing the following:
set -x OIDC_OP_AUTHORIZATION_ENDPOINT "https://login.microsoftonline.com/fcee251/oauth2/v2.0/authorize"
set -x OIDC_OP_TOKEN_ENDPOINT "https://login.microsoftonline.com/fcee251/oauth2/v2.0/token"
set -x OIDC_RP_CLIENT_ID "36ad9"
set -x OIDC_RP_CLIENT_SECRET "aead6"
set -x OIDC_OP_JWKS_ENDPOINT "https://login.microsoftonline.com/common/discovery/v2.0/keys"
set -x OIDC_RP_SIGN_ALGO "RS256"
set -x OIDC_USE_NONCE False
# used by 'login/management/commands/demo_data_login_oidc.py'
set -x KB_TEST_EMAIL_FOR_OIDC "patrick@kbsoftware.co.uk"
set -x KB_TEST_EMAIL_USERNAME "pkimber"
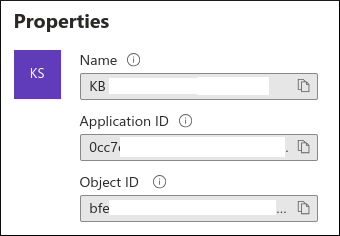
The Application ID (OIDC_RP_CLIENT_ID) is on the Overview page:
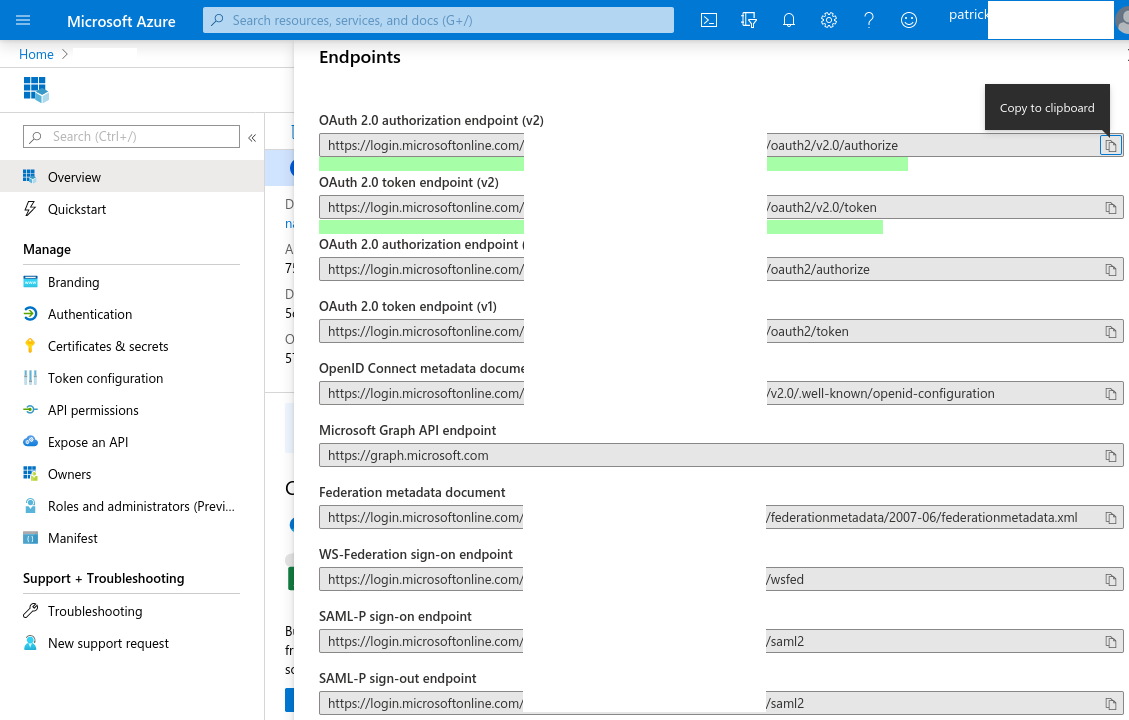
The OIDC_OP_AUTHORIZATION_ENDPOINT and OIDC_OP_TOKEN_ENDPOINT endpoints
are found by clicking on Endpoints
Create a secret in Certificates and secrets (OIDC_RP_CLIENT_SECRET):
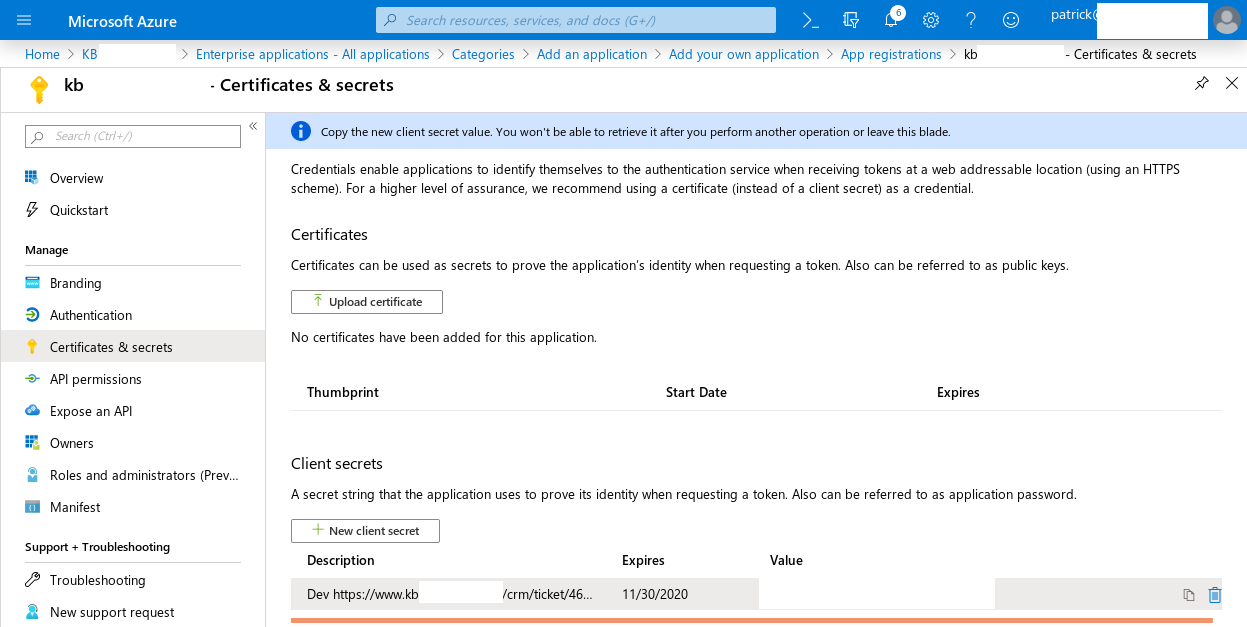
Tip
Copy the secret (not the id of the secret).
To get the OIDC_OP_JWKS_ENDPOINT and OIDC_RP_SIGN_ALGO
browse to:
https://login.microsoftonline.com/common/v2.0/.well-known/openid-configuration
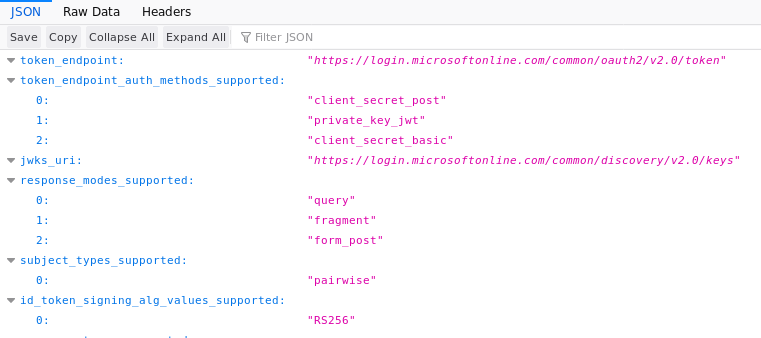
Tip
I found this information in the Fetch the OpenID Connect metadata document…
ssh
If your ssh connections are timing out, then add the following to your
~/.ssh/config file:
Host www.hatherleigh.info
ServerAliveInterval 120
ServerAliveCountMax 4
Tip
Replace Host as appropriate.